最近登录Linode某台服务器时,发现有个提示信息:
Last failed login: Tue May 23 01:52:58 UTC 2017 from 116.31.116.40 on ssh:notty There were 6727 failed login attempts since the last successful login. Last login: Tue May 23 01:46:01 2017 from 1.2.3.4
[root@mail ~]
#
这个IP一查,是广东的。这仅是几千次错误当中的最后一次。
服务器暴露在公网,则必然会有来自各地区各式各样的人,想对你的服务器进行穷举破解。
那就想办法block吧,连都不让它连接吧。首先想到防火墙。
因服务器是CentOS7的,它默认安装的是firewall, 并不是我们常说的iptables
下面就2个思路了。
1,直接用firewall , 把该IP添加拒绝;
2, 停用 firewall 改用iptables, 按iptables 的规则进行添加拒绝
省点事吧,选方案1好了。
[root@server ~]# firewall-cmd --permanent --add-rich-rule='rule family=ipv4 source address="116.31.116.40" drop'
[root@server ~]
# systemctl restart firewalld
[root@server ~]
#
这时候注销出来再重新登录,就没有刚才的提示了。
因为之前是对方能连接,但无法登录。而现在直接不让连接了。
也就是之前还有对话的机会,现在直接是不理你了。
不过,很快,对方更换了个IP,又来穷举了。看来这货代理或者是肉机不少哇。
那就先来土办法,继续添加先,同时大脑考虑着怎么使用白名单或者区域IP了
[root@server ~]# firewall-cmd --permanent --add-rich-rule='rule family=ipv4 source address="61.177.172.62" drop'
[root@server ~]
# systemctl restart firewalld
[root@server ~]
#
Linode 是个不错的服务商。会提供比较多的关于服务器维护方面的文档。这里就提到了 使用 Fail2Ban的这个工具
https://www.linode.com/docs/security/using-fail2ban-for-security
[root@server ~]# yum install fail2ban
[root@server ~]
# systemctl start fail2ban
[root@server ~]
# systemctl enable fail2ban Created symlink from /etc/systemd/system/multi-user.target.wants/fail2ban.service to /usr/lib/systemd/system/fail2ban.service.
因为.local的配置会override .conf 的配置,所以一般建议不动.conf 的配置,而是复制一份,要修改而在.local 上进行修改。
[root@server ~]# cp /etc/fail2ban/fail2ban.conf /etc/fail2ban/fail2ban.local
[root@server ~]
# cp /etc/fail2ban/jail.conf /etc/fail2ban/jail.local
因为是CentOS 7,默认没打开任何jail, 手工修改一下 jail.local ,将 shhd 的支持打开。
[sshd] enabled = true
同时还要将jail.local 里面的 backend = auto 改成 backend = systemd
修改完成后重启服务systemctl restart fail2ban.service
查看状态:
[root@ ~]# systemctl status fail2ban.service
● fail2ban.seserverrvice - Fail2Ban Service
Loaded: loaded (/usr/lib/systemd/system/fail2ban.service; enabled; vendor preset: disabled)
Active: active (running) since Tue 2017-05-23 07:32:31 UTC; 5s ago
Docs: man:fail2ban(1)
Process: 14519 ExecStart=/usr/bin/fail2ban-client -x start (code=exited, status=0/SUCCESS)
Main PID: 14522 (fail2ban-server)
CGroup: /system.slice/fail2ban.service
└─14522 /usr/bin/python2 -s /usr/bin/fail2ban-server -s /var/run/fail2ban/fail2ban.sock -p /var/run/fail2ban/fail2ban.pid...
May 23 07:32:31 server.google.com systemd[1]: Starting Fail2Ban Service...
May 23 07:32:31 server.google.com fail2ban-client[14519]: 2017-05-23 07:32:31,580 fail2ban.server [14520]: INFO St...0.9.6
May 23 07:32:31 server.google.com fail2ban-client[14519]: 2017-05-23 07:32:31,581 fail2ban.server [14520]: INFO St... mode
May 23 07:32:31 server.google.com systemd[1]: Started Fail2Ban Service.
Hint: Some lines were ellipsized, use -l to show in full.
[root@server ~]
#
查看日志:
tail -f /var/log/fail2ban.log
会发现一些Ban 以及unban 的情况。原来默认的是设置10分钟。
手工修改一下 jail.local 里面的 bantime=600 ,默认是600秒,也就是10分钟。改成一个更大的数值,172800 也就是二天。
[root@server ~]# tail -f /var/log/fail2ban.log 2017-05-23 12:21:51,391 fail2ban.actions [14899]: NOTICE [sshd] Ban 212.129.15.136 2017-05-23 13:35:06,361 fail2ban.filter [14899]: INFO [sshd] Found 123.56.67.13 2017-05-23 13:35:06,376 fail2ban.filter [14899]: INFO [sshd] Found 123.56.67.13 2017-05-23 13:35:08,546 fail2ban.filter [14899]: INFO [sshd] Found 123.56.67.13 2017-05-23 13:35:08,930 fail2ban.actions [14899]: NOTICE [sshd] Ban 123.56.67.13 2017-05-23 13:48:51,130 fail2ban.filter [14899]: INFO [sshd] Found 190.48.84.35 2017-05-23 13:48:51,737 fail2ban.filter [14899]: INFO [sshd] Found 190.48.84.35 2017-05-23 13:48:52,895 fail2ban.filter [14899]: INFO [sshd] Found 190.48.84.35 2017-05-23 13:48:53,139 fail2ban.actions [14899]: NOTICE [sshd] Ban 190.48.84.35 2017-05-23 13:48:53,503 fail2ban.filter [14899]: INFO [sshd] Found 190.48.84.35 2017-05-23 14:10:17,283 fail2ban.filter [14899]: INFO [sshd] Found 64.187.217.234 2017-05-23 14:10:17,473 fail2ban.filter [14899]: INFO [sshd] Found 64.187.217.234 2017-05-23 14:10:19,590 fail2ban.filter [14899]: INFO [sshd] Found 64.187.217.234 2017-05-23 14:10:19,779 fail2ban.filter [14899]: INFO [sshd] Found 64.187.217.234 2017-05-23 14:10:19,924 fail2ban.actions [14899]: NOTICE [sshd] Ban 64.187.217.234 2017-05-23 14:10:22,317 fail2ban.filter [14899]: INFO [sshd] Found 64.187.217.234 2017-05-23 14:10:22,494 fail2ban.filter [14899]: INFO [sshd] Found 64.187.217.234 2017-05-23 14:10:23,150 fail2ban.actions [14899]: NOTICE [sshd] 64.187.217.234 already banned
会发现fail2ban有提示将一些IP加入ban.是否真的Ban了呢?
因初次接触fail2ban,我对它的理解就是它是监测一些系统、应用的日志,然后再将规则加入到系统现有的防火墙中。
update:
后来看了官方的说明,我都服了我自己了。原理确实是如此:
Fail2ban scans log files (e.g. /var/log/apache/error_log) and bans IPs that show the malicious signs — too many password failures, seeking for exploits, etc. Generally Fail2Ban is then used to update firewall rules to reject the IP addresses for a specified amount of time, although any arbitrary other action (e.g. sending an email) could also be configured. Out of the box Fail2Ban comes with filters for various services (apache, courier, ssh, etc).
无意中用 iptables -L查看了下
发现这些被Ban的IP,貌似是加入到了iptables的列表中。
[root@server ~]# iptables -L Chain INPUT (policy ACCEPT) target prot opt source destination f2b-sshd tcp -- anywhere anywhere multiport dports ssh ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED ACCEPT all -- anywhere anywhere INPUT_direct all -- anywhere anywhere INPUT_ZONES_SOURCE all -- anywhere anywhere INPUT_ZONES all -- anywhere anywhere ACCEPT icmp -- anywhere anywhere REJECT all -- anywhere anywhere reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT) target prot opt source destination ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED ACCEPT all -- anywhere anywhere FORWARD_direct all -- anywhere anywhere FORWARD_IN_ZONES_SOURCE all -- anywhere anywhere FORWARD_IN_ZONES all -- anywhere anywhere FORWARD_OUT_ZONES_SOURCE all -- anywhere anywhere FORWARD_OUT_ZONES all -- anywhere anywhere ACCEPT icmp -- anywhere anywhere REJECT all -- anywhere anywhere reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT) target prot opt source destination OUTPUT_direct all -- anywhere anywhere Chain FORWARD_IN_ZONES (1 references) target prot opt source destination FWDI_iredmail all -- anywhere anywhere [goto] FWDI_iredmail all -- anywhere anywhere [goto] Chain FORWARD_IN_ZONES_SOURCE (1 references) target prot opt source destination Chain FORWARD_OUT_ZONES (1 references) target prot opt source destination FWDO_iredmail all -- anywhere anywhere [goto] FWDO_iredmail all -- anywhere anywhere [goto] Chain FORWARD_OUT_ZONES_SOURCE (1 references) target prot opt source destination Chain FORWARD_direct (1 references) target prot opt source destination Chain FWDI_iredmail (2 references) target prot opt source destination FWDI_iredmail_log all -- anywhere anywhere FWDI_iredmail_deny all -- anywhere anywhere FWDI_iredmail_allow all -- anywhere anywhere Chain FWDI_iredmail_allow (1 references) target prot opt source destination Chain FWDI_iredmail_deny (1 references) target prot opt source destination Chain FWDI_iredmail_log (1 references) target prot opt source destination Chain FWDO_iredmail (2 references) target prot opt source destination FWDO_iredmail_log all -- anywhere anywhere FWDO_iredmail_deny all -- anywhere anywhere FWDO_iredmail_allow all -- anywhere anywhere Chain FWDO_iredmail_allow (1 references) target prot opt source destination Chain FWDO_iredmail_deny (1 references) target prot opt source destination Chain FWDO_iredmail_log (1 references) target prot opt source destination Chain INPUT_ZONES (1 references) target prot opt source destination IN_iredmail all -- anywhere anywhere [goto] IN_iredmail all -- anywhere anywhere [goto] Chain INPUT_ZONES_SOURCE (1 references) target prot opt source destination Chain INPUT_direct (1 references) target prot opt source destination Chain IN_iredmail (2 references) target prot opt source destination IN_iredmail_log all -- anywhere anywhere IN_iredmail_deny all -- anywhere anywhere IN_iredmail_allow all -- anywhere anywhere Chain IN_iredmail_allow (1 references) target prot opt source destination ACCEPT tcp -- anywhere anywhere tcp dpt:http ctstate NEW ACCEPT tcp -- anywhere anywhere tcp dpt:submission ctstate NEW ACCEPT tcp -- anywhere anywhere tcp dpt:pop3s ctstate NEW ACCEPT tcp -- anywhere anywhere tcp dpt:smtp ctstate NEW ACCEPT tcp -- anywhere anywhere tcp dpt:imaps ctstate NEW ACCEPT tcp -- anywhere anywhere tcp dpt:pop3 ctstate NEW ACCEPT tcp -- anywhere anywhere tcp dpt:ssh ctstate NEW ACCEPT tcp -- anywhere anywhere tcp dpt:https ctstate NEW ACCEPT tcp -- anywhere anywhere tcp dpt:imap ctstate NEW Chain IN_iredmail_deny (1 references) target prot opt source destination DROP all -- 61.177.172.62 anywhere DROP all -- 116.31.116.40 anywhere Chain IN_iredmail_log (1 references) target prot opt source destination Chain OUTPUT_direct (1 references) target prot opt source destination Chain f2b-sshd (1 references) target prot opt source destination REJECT all -- 114.252.66.27 anywhere reject-with icmp-port-unreachable REJECT all -- 64.187.217.234 anywhere reject-with icmp-port-unreachable REJECT all -- 190-48-84-35.speedy.com.ar anywhere reject-with icmp-port-unreachable REJECT all -- 123.56.67.13 anywhere reject-with icmp-port-unreachable REJECT all -- 212-129-15-136.rev.poneytelecom.eu anywhere reject-with icmp-port-unreachable REJECT all -- 58.240.52.75 anywhere reject-with icmp-port-unreachable REJECT all -- 119.193.140.155 anywhere reject-with icmp-port-unreachable REJECT all -- u19784916.onlinehome-server.com anywhere reject-with icmp-port-unreachable REJECT all -- 78-56-143-236.static.zebra.lt anywhere reject-with icmp-port-unreachable REJECT all -- 211.220.207.201 anywhere reject-with icmp-port-unreachable REJECT all -- 182.38.15.7 anywhere reject-with icmp-port-unreachable REJECT all -- 212-129-60-174.rev.poneytelecom.eu anywhere reject-with icmp-port-unreachable REJECT all -- 79.124.59.202 anywhere reject-with icmp-port-unreachable REJECT all -- 59.45.175.36 anywhere reject-with icmp-port-unreachable RETURN all -- anywhere anywhere
[root@server ~]
#
可是我是CentOS 7,系统默认用的firewalld啊!
再查看一下这个firewalld相关的规则,空空如也
[root@server ~]# firewall-cmd --direct --get-all-rules
[root@server ~]
# firewall-cmd –direct –get-all-chains
[root@server ~]
#
所以问题来了:
从fail2ban的日志来看,用户确实是试了几次然后挨BAN了,就换IP了。因为没看到像之前那样同一IP有大量的Fail的记录,--从这角度看fail2ban 似乎起作用;
但是从iptables -L列出的规则来看,fail2ban加的这些ban的IP,是加到了iptables上去了。
可是我的centos 默认使用的是firewalld,并没有使用iptables.
所以这事没完!!不要以为安装个fail2ban就完事了。
还得继续探究!!于是有必要深入理解firewalld 和 iptables的实现原理了。
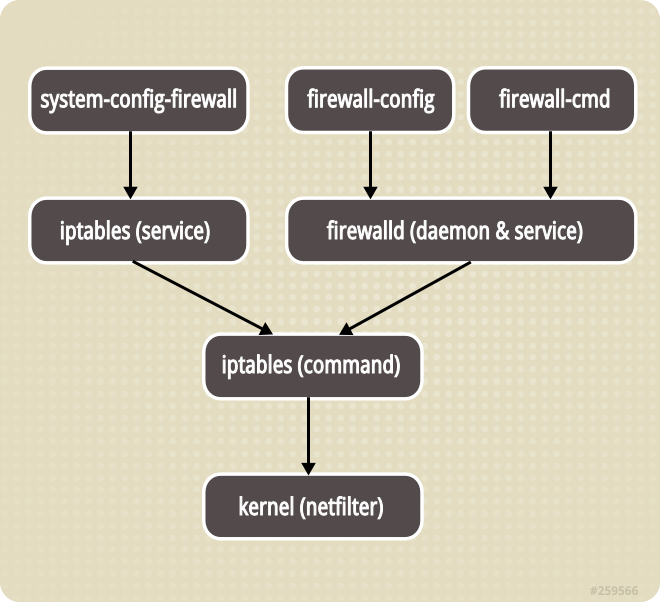
网络搜寻之下(ref: http://www.cnblogs.com/pixy/p/5156739.html), 发现了这样一句话,CentOS7默认采用的是firewalld管理netfilter子系统,底层调用的仍然是iptables命令
还有一张图,如下:
这样一来,就解释得通了。
下面要深挖的可就是 netfilter了,有空时可以研究一下:
ref: https://www.digitalocean.com/community/tutorials/a-deep-dive-into-iptables-and-netfilter-architecture
其它方案1:
将ssh的默认端口22,修改成其它的。这样可以避开相当部分的这些扫描客了。
vi /etc/ssh/sshd_config ... #Port=22
将注释的#号去除,并将默认的22端口改成其它的端口。然后生启sshd
services sshd restart
systemctl restart sshd.service
其它方案2: 直接取消账号密码的方式登录,改用key的方式进行登录
可以参考这个文档: https://wiki.centos.org/HowTos/Network/SecuringSSH#head-9c5717fe7f9bb26332c9d67571200f8c1e4324bc
大体步骤是就用工具(不管是Xshell自带的或者是Linux系统自带的ssh-keygen)生成一对密钥。
一个公钥,一个私钥。
私钥用于客户端(比如连接用的Xshell/putty等,理解为客户端)
公钥用于服务端(存放于/.ssh/authorized_keys –为什么一定是这个文件名? 未必!不过这是ssh默认的,完全可以通过修改配置文件 sshd_config 来实现使用其它的文件名。#AuthorizedKeysFile %h/.ssh/authorized_keys )
转载请注明:Linc Hu » 捣腾记录:CentOS 7 从ban IP起安全加固防破解